Protect your business from these seven common types of cyber attacks.
Cybercriminals use different tools and techniques to attack businesses. For instance, a cyberattack halted all urgent surgeries in Czech Republic’s busy hospital fighting against COVID-19. A food delivery company in Germany fell victim to a distributed denial-of-service (DDoS) attack, resulting in a huge loss due to halted deliveries. Government officials in the U.S. received a slew of phishing attacks after a relief bill was passed.
Predictions by Gartner claim that cybercriminals will have weaponized operational technology (OT) environments by 2025 to harm or kill humans. This suggests that cyberattack techniques will continue evolving to come up with better malware versions that result in bigger losses for businesses.
This situation is more concerning for small and midsize businesses (SMBs), as they don’t have the same resources to fight cyberattacks as large enterprises. As an SMB owner, you need to build a defense mechanism and prepare your team to cut the losses resulting from cybercrime.
In this article, we’ve listed the seven most common cyberattacks and shared some tips to prevent them. Educate yourself and your team about these cyberattacks to build awareness and prevent cybercrime.
Find providers that can help with your business needs by using our lists of managed service providers agencies by location.
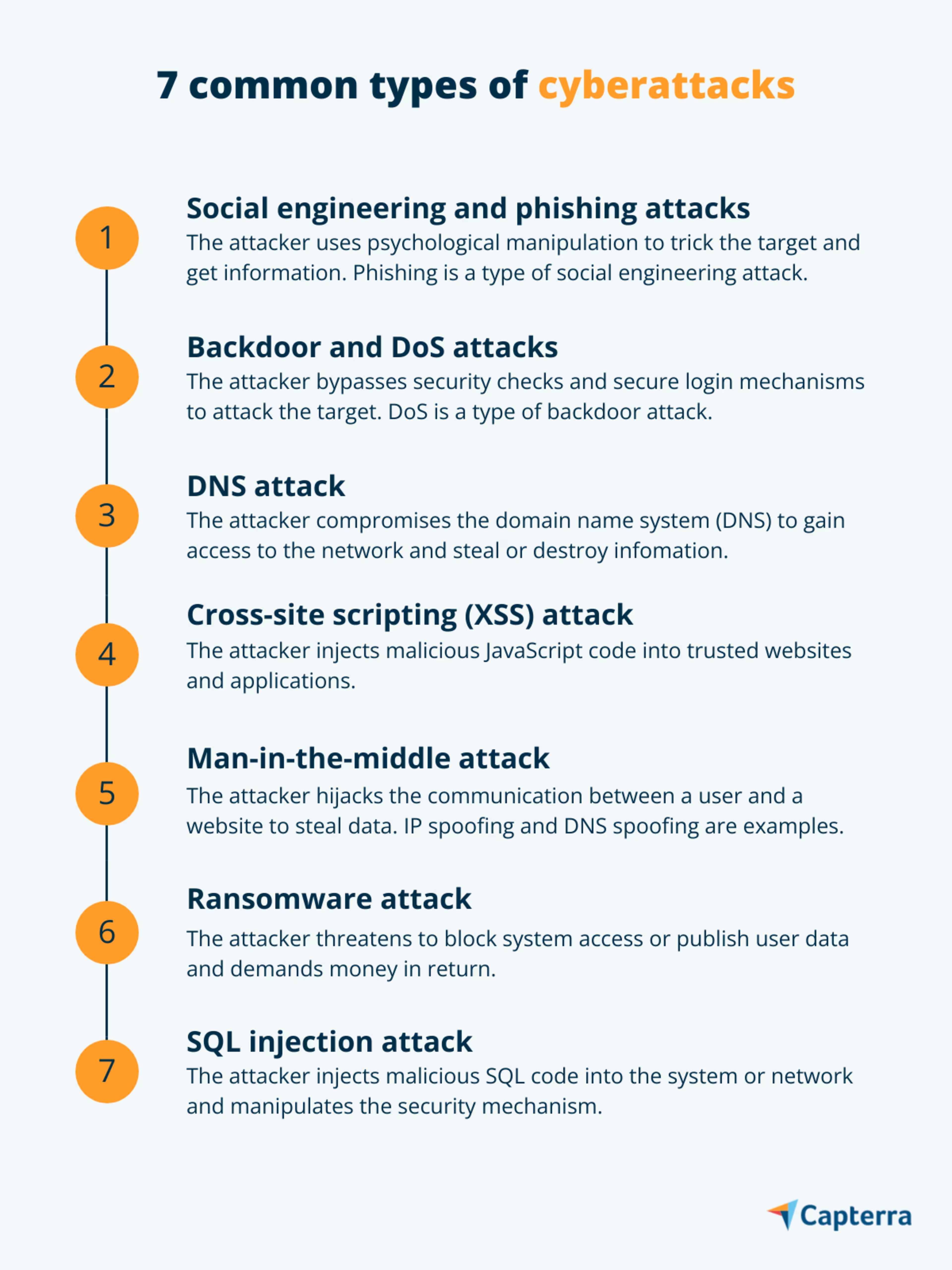
1. Social engineering and phishing attack
A social engineering attack manipulates the target to get access to confidential information. The attacker uses psychological manipulation—i.e., influencing through emotional exploitation—to trick the target into giving information such as bank details or passwords.
Phishing is a commonly used social engineering attack wherein a cyber criminal uses emails or website ads to manipulate the target and get information. Most SMBs are targeted by phishing attacks because they have a small network, and it’s easy for the attacker to identify who is more likely to fall prey and disclose information.
What makes a social engineering attack dangerous is that it takes advantage of human errors rather than technology loopholes. The attack could be in the form of a message from a friend/colleague, an email asking for donations, a message from an unknown person, or a promotional email with a “too good to be true” offer.
Besides phishing, these are some other types of social engineering attacks:
Baiting: Attackers plant physical or online baits such as leaving a malware-infected flash drive at a public place or putting up an enticing ad that leads to a spam website or landing page.
Scareware: Attackers send threat notifications prompting users to install software that offers protection against cyberattacks.
Pretexting: Attackers create a scenario to trick the target and convince them to disclose business or personal information (e.g., sending an email pretending to be a business partner asking for information about a project that’s not yet launched).
Spear phishing: Attackers send emails targeting a person or business (e.g., sending an email pretending to be an HR partner asking employees to sign a yearly handbook).
Tips to prevent social engineering attacks:
Be aware of tempting offers and schemes
Keep your antivirus/antimalware updated
Don’t open emails and attachments from suspicious sources
Use multi-factor authentication to protect your account and systems
Use a link expander to check links before clicking them
2. Backdoor and DoS attack
A backdoor attack gains access to a computer system or encrypted data by bypassing security checks and login mechanisms. The attack negates the authentication process for secure login and allows access to applications, networks, or devices carrying sensitive information. The attack also allows remote launching of commands and updating of malware.
A denial-of-service (DoS) attack is one of the malicious activities that a backdoor attack can lead to. In a DoS attack, the attacker floods the target system or network with unusual traffic that causes a temporary or permanent denial of service to the users. When this technique is used to hack multiple devices (laptop, smartphone, etc.) in a corporate network, it’s known as DDoS attack.
Other types of backdoor attacks include:
Built-in backdoor: A backdoor entry is created for engineers while programming a software tool to directly access its HTML code and fix bugs. Cyber criminals take advantage of this backdoor to hack the system and access sensitive information or plant a virus into devices that have the software.
Trojan backdoor: A malicious software program that, if downloaded, gives unauthorized system access to the attacker. It’s specially designed for hacking high-security systems and resources.
Tips to prevent backdoor attacks:
Avoid clicking on or downloading from suspicious links
Get your devices inspected regularly, especially the ones used for sensitive data
Have firewall and antivirus on your devices and systems, and install timely updates
Use an anti-malware tool
3. DNS attack
Domain name system (DNS) is like a phonebook that translates machine-friendly IP addresses into human-readable URLs. This makes DNS a crucial component for businesses as well as a prime target for cyberattacks.
During a DNS attack, the domain name system is compromised, allowing the attacker to gain access to the network and steal or destroy information. Here are the different types of cyberattacks involving the DNS security threat:
DNS tunneling: Attackers use a DNS resolver to create a tunnel between the victim and the attacker. This tunnel allows the malware to pass security checks and reach the victim.
Domain generation algorithm: Attackers generate new domains and IP addresses, as the security software blocks the previous ones. This helps them escape the security measures and continue attempting attacks.
Fast flux: Attackers use multiple fake domains and IP addresses to confuse and escape IP controls and enter a secure network.
Newly registered domains: Attackers create variations of existing domains to fool the users. These domains are available only for a short period, making them difficult to detect.
Tips to prevent DNS attacks:
Audit your DNS zones
Update your DNS servers
Restrict DNS servers for zone transfers—i.e., replicating zone files to multiple DNS servers
Use multi-factor authentication for system and network logins
Set up comprehensive detection and response systems
4. Cross-site scripting (XSS) attack
Cross-site scripting—also known as an XSS attack—is a technique that manipulates networks or applications to send malicious JavaScript code to the users’ browser. Simply put, the attacker injects malicious code into trusted websites and applications.
When a user visits a compromised website, the communication path between the user and the platform is hacked by the attacker. This way, the attacker can steal important information, such as bank details and login credentials, or perform actions on behalf of the user.
Types of cyberattacks involving XSS include:
Reflected XSS: The attacker sends malicious code to a user’s browser through a compromised network or application.
Stored XSS: The attacker injects malicious code directly into a user’s browser.
DOM-based XSS: The attacker modifies the client-side code on a compromised network or application.
Tips to prevent XSS attacks:
Mitigate risks using a content security mechanism
Filter user data that is being received, and encode data that is going out to the user
Use a web vulnerability scanner to check for any compromised network or application
5. Man-in-the-middle attack
Man-in-the-middle (MITM) is a type of cyberattack where the attacker hijacks the communication between a user and a website and secretly monitors it to steal information. It creates a similar-looking website but with a virus in its code that enables eavesdropping.
For example, you receive an email from your bank asking you to update your KYC for internet banking. You’ll likely believe the communication and start following the instructions. However, this process is being monitored by an attacker who’s planted a virus in the website, and the information (bank details, login credentials, or KYC details) you enter is visible to the attacker.
Here are the different types of MITM attacks:
IP spoofing: Attackers mask the identity of malware and present it to users as a legitimate link to gain access to resources.
DNS spoofing: Attackers intercept DNS requests and redirect users to malicious sites that resemble the original.
HTTPS spoofing: Attackers replace the characters of a secured domain with non-ASCII characters that are similar to the original.
Email hijacking: Attackers gain unauthorized access to a user’s email account and monitor communications for malicious purposes.
Wi-Fi eavesdropping: Attackers trick users to connect to a malicious network by naming it as an actual Wi-Fi network. This attack is also known as an evil twin attack.
SSL stripping: Attackers downgrade the communication between two targets into an unencrypted format to launch an MITM attack.
Tips to prevent MITM attacks:
Inspect current Wi-Fi connections
Avoid connecting to public networks
Use a network sniffer
Look out for repeated or unexpected disconnections
Check strange addresses in the browser bar
Check network connections to unfamiliar locations
6. Ransomware attack
About 27% of malware incidents reported in 2020 were due to ransomware, according to Gartner. This makes ransomware one of the prominent types of cyberattacks that threaten to publish a victim’s data or block access, demanding money or ransom in return.
While already prevalent, ransomware attacks have surged with the pandemic-induced remote work environment, alarming security and risk leaders to tighten their cybersecurity methods. Though uncommon, a ransomware attack can even result in shutting down the business.
Here are the types of ransomware attacks:
Locker ransomware: Attackers lock users completely out of their system or lock basic computer functions, with the ransom amount displayed on a lock screen.
Crypto ransomware: Attackers encrypt users’ files and documents. While users can still see their data on the system, they cannot access it without a decryption key.
Tips to prevent ransomware attacks:
Conduct regular ransomware assessments
Maintain consistent operations readiness
Enforce ransomware governance
Educate and train stakeholders and staff on ransomware response actions
Employ a ransomware defender
Use whitelisting and anti-ransomware tools
Monitor anomalous file activities such as failed modification attempts
7. SQL injection attack
SQL injection (SQLi) is a type of cyberattack that uses the structured query language (SQL) code to manipulate a network’s or system’s security and gain access to information. Once injected into the system or network, the SQL code enables the attacker to steal, delete, or modify information, resulting in a data breach.
The different types of SQLi attacks include:
In-band SQLi: Attackers use the same channel to launch the attack and gather information.
Inferential SQLi: Attackers send data to the server and observe responses to learn more about its structure.
Out-of-band SQLi: Attackers use the capacity of the server to create DNS or HTTPS requests and transfer data.
Tips to prevent SQLi attacks:
Write codes that can identify illegitimate user inputs
Use a firewall to detect and weed out SQLi attacks
Use data-centric strategies to focus on data protection along with network and application protection
Use an SQL compliance manager tool
Additional resources to help prevent cyberattacks
Technology controls and employee awareness go hand in hand when it comes to preventing cyberattacks. There are plenty of cybersecurity tools and security awareness training software that can help you build a defense mechanism against cyberattacks.
Educate yourself and your team members about cybersecurity and learn the ways to ensure secure behavior, not just at the workplace but all the time. Check out these related articles on cybersecurity:

